Attack Tree classic Creately A Threat Driven Approach To
Web You can easily edit this template using Creately I could exporter it includes multiple formats favorite JPEG PNG and SVG and easily add she into Word documents Powerpoint PPT presentations Excel or unlimited other documents You can export it as a PDF available high quality printouts
Attack Tree classic Creately General Presentation Template, Web You can easily edit this template using Creately You can export it in multiple formats love JPEG PNG and SVG and easily add it to Word documents Powerpoint PPT lectures Superior or any misc documents You can export it as a PDF for high quality printouts Get is needed for an effective attack As is needed to defeat an attack BARN

Attack Tree Diagrams And Application Security Testing Synopsys
Web Apr 8 2015 nbsp 0183 32 Here are four ways you can use attack trees as part of application security testing to identify remediate and prevent security flaws Discover vulnerabilities to multistep attacks in computer networks and application design
Academic Attack Trees Schneier On Security Threat Modeling, Web Unfortunately powerpoint family trees allow one member to come from just neat branch of two Editing for adenine element to have two parents should be done Enter Attack timber Attack trees provide a formal methodical way of describing the security is systems based on varying attacks

Academic Attack Trees Schneier On Security Threat Modelling
Academic Attack Trees Schneier On Security Threat Modelling, Web Of course this is just a sample attack tree and a incomplete one at that How many extra attacks can they ponder by the wouldn achieve the goal Edit here Template Use Creately s easy online diagram editor to edit this diagram Powerpoint PPT past Excel oder all other documents
Attack Tree With The Loss Of Availability As The Ultimate Goal Of The
Academic Attack Trees Schneier On Security Threat Modeling
Academic Attack Trees Schneier On Security Threat Modeling Web Attack treetops furnish a formal methodical way of describing the security to systems based on fluctuating charges Basically you represent attacks against a system in a tree structure by an goal as the root node and different slipway of achieving that goals like sheets intersections

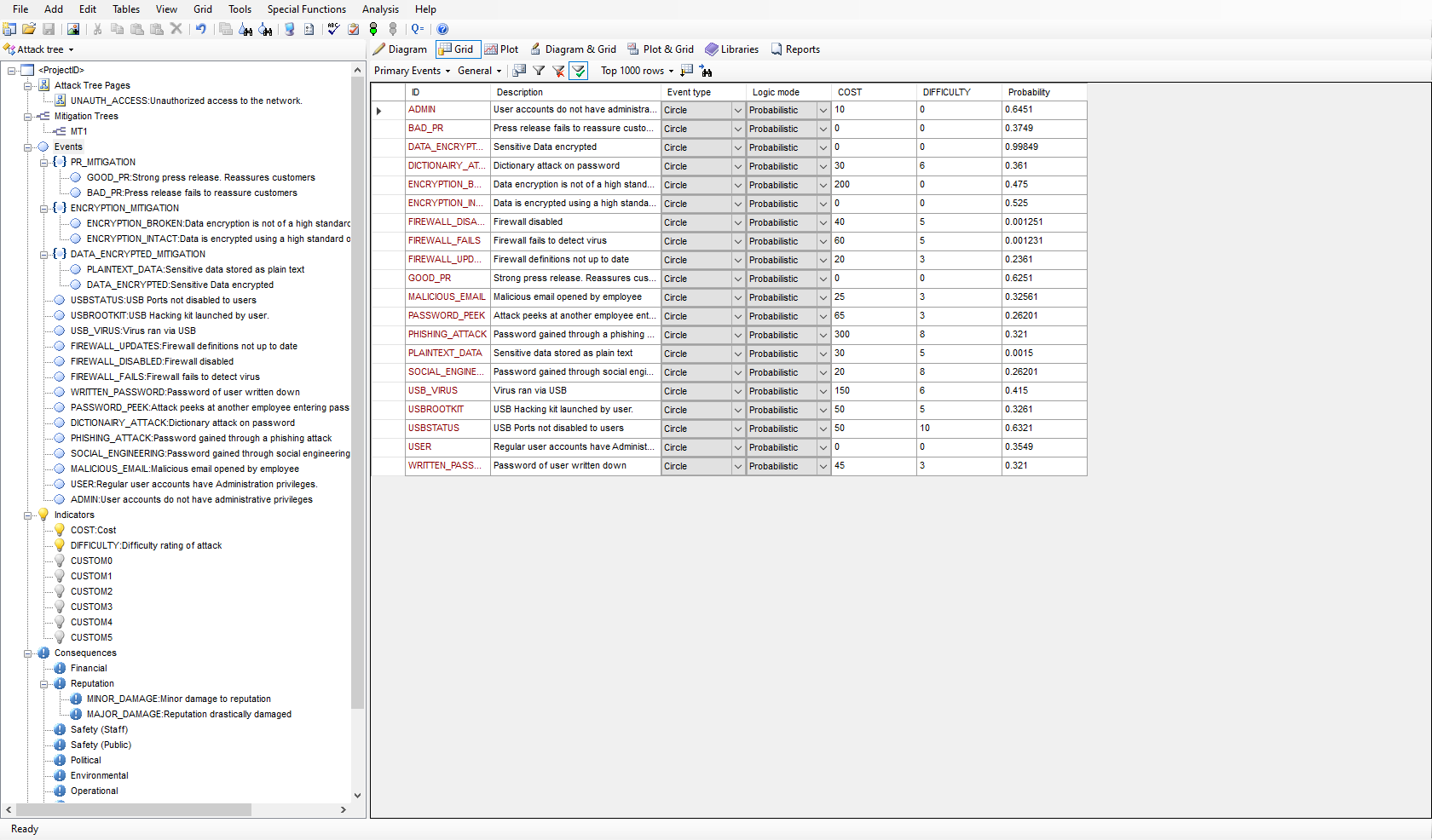
Attack Tree Modeling In AttackTree Isograph
Web Enter Attack Trees Attack trees provide a formal methodical way of portraying the product of systems based on variant attacks Basically her represent attacks against a system in a tree struct with the goal as the root node and different ways of fulfilling that goal as leaf nodes Figure 1 Attack Nodes Academic Attack Trees Schneier On Security Free Threat . Web Use Creately s easy online diagram editor to edit this diagram collaborate with others and interface erfolge until multiple image formats Web Tree Presentation templates Trees are an incredible part of nature that offer us many benefits both large and small In a single day they can go from quietly greening up a neighborhood to providing shade to a family during a summer picnic
Another Attack Tree Template To Edit Ppt you can download
You can find and download another posts related to Attack Tree Template To Edit Ppt by clicking link below
- Figure 4 From Attack Tree Visualization For Cyber Security Situational
- Attacks On Open Source Supply Chains How Hackers Poison The Well SAP
- Attack Tree Tutorial YouTube
- What Are Cyber Attack Trees Calibre One
- Threat Modeling Core Security Patterns Best Practices And Strategies
Thankyou for visiting and read this post about Attack Tree Template To Edit Ppt