An Example Attack Tree Download Scientific Diagram
WEB Download scientific diagram An example attack tree from publication Evaluation of complex security scenarios using defense trees and economic indexes In this article we present
Example Attack Tree Download Scientific Diagram, WEB The leaves of the attack tree unlike a fault tree are the discrete actions that must be taken to achieve the objective An example of an attack tree appears in Fig fault

Guide To Threat Modeling Using Attack Trees
WEB Feb 22 2024 nbsp 0183 32 An attack tree is a graphical representation of the various steps an attacker might take to exploit vulnerabilities and achieve specific malicious goals It provides a visual and organized way to model the attack paths potential vulnerabilities and
Attack Tree Diagrams And Application Security Testing, WEB Apr 7 2015 nbsp 0183 32 This is an example of an attack tree diagram a methodological graphical representation of an attack from the perspective of the attacker Attack trees like this one have been used to identify security vulnerabilities in all types of complex systems such as supervisory controls and data acquisition SCADA networks biometric systems and

Attack Tree Wikipedia
Attack Tree Wikipedia, WEB Open source Commercial See also References Attack trees are conceptual diagrams showing how an asset or target might be attacked 1 Attack trees have been used in a variety of applications In the field of information technology they have been used to describe threats on computer systems and possible attacks to realize those threats

An Attack Tree Example Download Scientific Diagram
Attack Tree Creately
Attack Tree Creately WEB Attack Tree Use Creately s easy online diagram editor to edit this diagram collaborate with others and export results to multiple image formats You can easily edit this template using Creately You can export it in multiple formats like JPEG PNG and SVG and easily add it to Word documents Powerpoint PPT presentations Excel or any

Threat Modeling Explained A Process For Anticipating Cyber Attacks
WEB Figure 1 Example visualization of an attack tree 2 Figure 2 DSRM Process Model Based on Peffers et al 2007 5 Figure 3 Research process diagram based on DSRM Process Model Peffers et al 2007 8 The Motivation Of Attackers In Attack Tree Analysis TU Delft. WEB Attack trees promised to bring greater rigor and objectivity to hostile risk analysis Unfortunately when I attempted to learn more about attack trees I discovered that there were very few references on the subject The few papers I found were either elementary or assumed that the reader already knew all about attack trees WEB This paper classifies attack trees in two dimensions proper trees vs directed acyclic graphs i e with shared subtrees and static vs dynamic gates
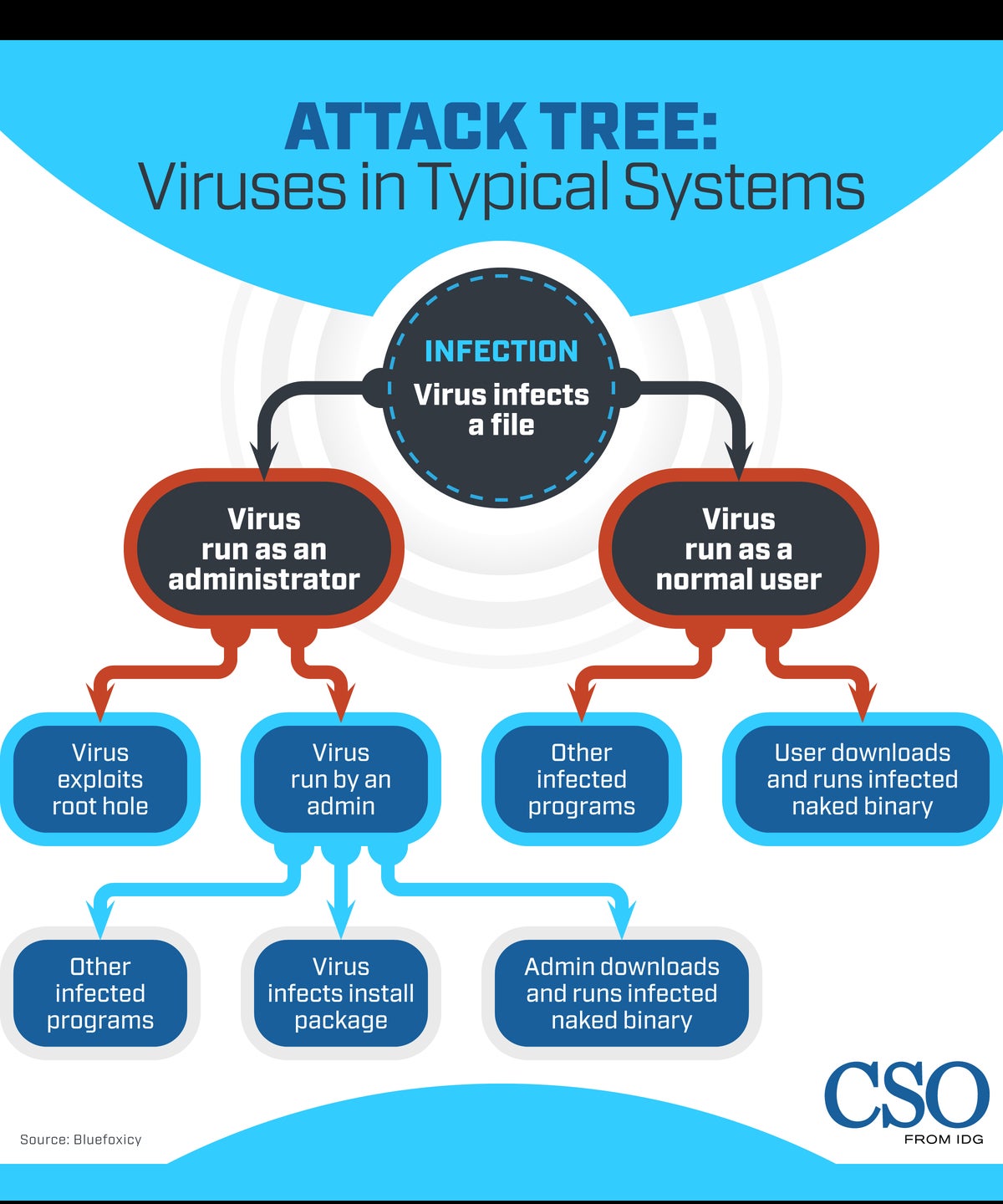
Another Example Attack Tree Download Scientific Diagram you can download
You can find and download another posts related to Example Attack Tree Download Scientific Diagram by clicking link below
- Example Of The Attack Tree For Computer Viruses Download Scientific
- Generic Attack Tree Structure Download Scientific Diagram
- Attack Tree Modeling In AttackTree Isograph
- How To Draw Attack Trees Stuffjourney Giggmohrbrothers
- What Is An Attack Tree YouTube
Thankyou for visiting and read this post about Example Attack Tree Download Scientific Diagram