A CISO s Guide To Risk Mitigation Strategies CyberArrow
4 days ago nbsp 0183 32 That s why smart CISOs use strong risk mitigation strategies to Protect business assets Ensure compliance Support business growth
How To Craft Cyber risk Statements That Work With Examples, Feb 15 2024 nbsp 0183 32 To write an effective cyber risk statement consider the following key steps Identify the risk Start by identifying potential cyber threats that put the business at risk These can

Mitigation Risk Management Key Strategies
Apr 29 2025 nbsp 0183 32 Learn how to identify assess and mitigate risks to improve security posture of your organization Cybersecurity risk mitigation is a set of
Threat Mitigation Examples Example 1 Mitigating Cybersecurity , 5 Mitigation Profile examples that illustrate how organizations may apply the Framework to 6 mitigate specific threats These scenarios include cybersecurity intrusion malware and insider

8 Top Strategies For Cybersecurity Risk Mitigation
8 Top Strategies For Cybersecurity Risk Mitigation, Jul 12 2021 nbsp 0183 32 Let s take a look at 8 key strategies for bolstering security and limiting the impact of successful attacks including conducting a risk

Risk Mitigation Puzzle PIeces Reduce Danger Security Problem SunXLium
Identifying And Estimating Cybersecurity Risk For Enterprise Risk
Identifying And Estimating Cybersecurity Risk For Enterprise Risk Documenting the likelihood and impact of various threat events through cybersecurity risk registers integrated into an enterprise risk profile helps to later prioritize and communicate

Nist Cybersecurity Framework Vs Iso Vs Nist Vs SexiezPicz Web Porn
Dec 8 2023 nbsp 0183 32 Building a strong risk mitigation strategy can set up an organization to have a strong response in the face of risk This ultimately can reduce the Building A Successful Risk Mitigation Strategy IBM. In this paper describe work in progress on a new quantitative model to assess aggregate information security risks that is currently under development for deployment We show how to Apr 16 2025 nbsp 0183 32 Phase 3 Risk Mitigation Strategies Uncertainty in projects cannot be eliminated but it can be mitigated Some broad mitigation strategies include
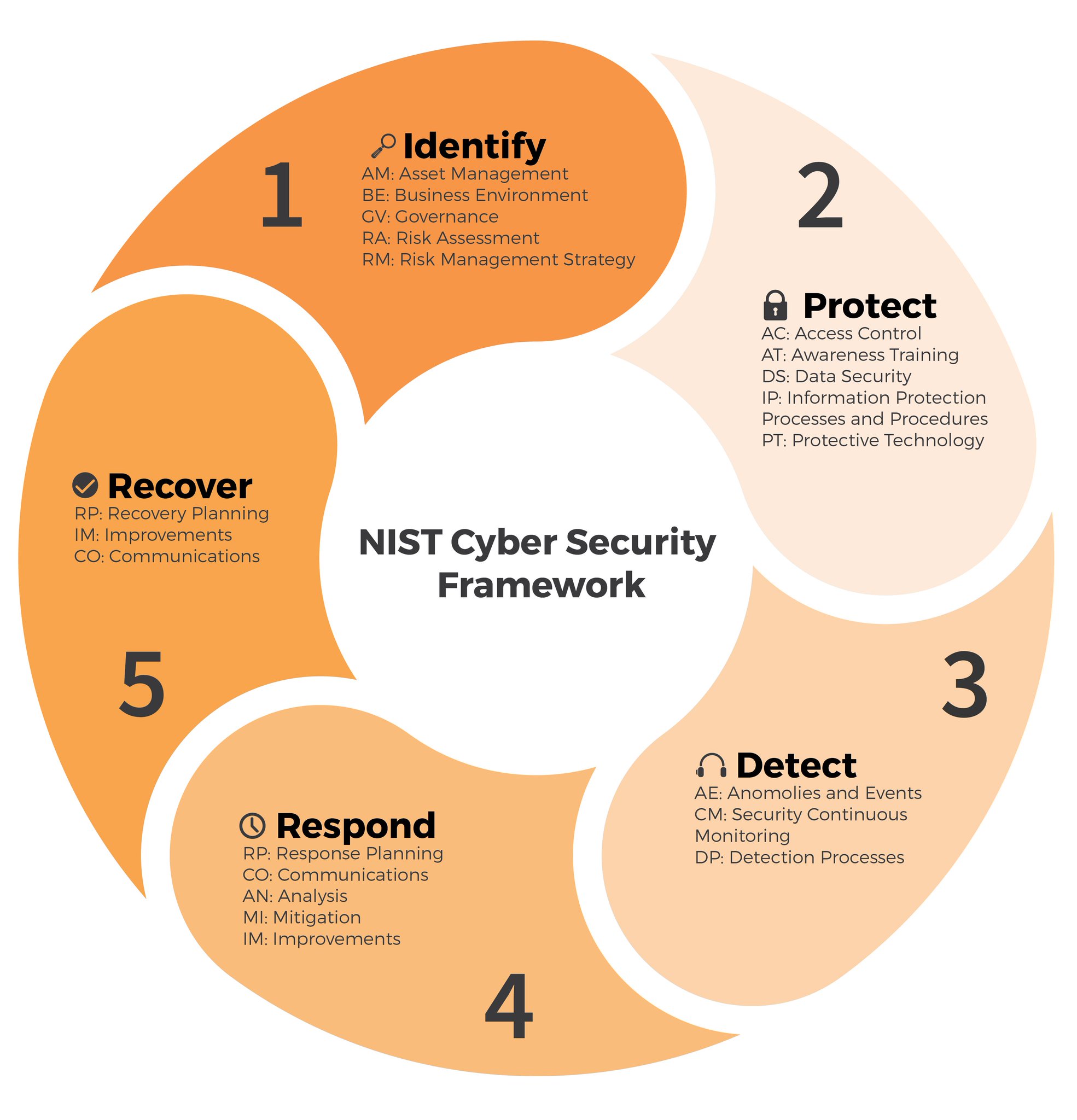
Another Information Security Risk Mitigation Strategy With Problem Statement you can download
You can find and download another posts related to Information Security Risk Mitigation Strategy With Problem Statement by clicking link below
- Risks And Mitigation Strategies Template Documents Global
- 5 Essential Risk Mitigation Strategies For Your Business Bleuwire
- Mitigation Plan Template
- Risk Mitigation Vs Risk Transfer What You Need To Know Before Buying
- Enterprise Risk Management Policy Template
Thankyou for visiting and read this post about Information Security Risk Mitigation Strategy With Problem Statement