What Is IT Security IBM
Jun 1 2023 nbsp 0183 32 What is IT security IT security which is short for information technology security is the practice of protecting an organization s IT assets computer systems networks digital
What Is AI Security IBM, May 15 2025 nbsp 0183 32 AI security means different things in different contexts While the focus of this page is the use of AI to improve cybersecurity two other common definitions center on securing AI

Physical Security In Cybersecurity IBM
Apr 7 2025 nbsp 0183 32 Most of us think of cybersecurity as a purely digital affair but cyberattacks can actually begin right here in the physical world
What Is Information Security IBM, Jul 26 2024 nbsp 0183 32 Information security InfoSec is the protection of important information against unauthorized access disclosure use alteration or disruption

What Is Data Security IBM
What Is Data Security IBM, What is data security Data security is the practice of protecting digital information from unauthorized access corruption or theft throughout its entire lifecycle This concept

Application User
What Is API Security IBM
What Is API Security IBM May 15 2025 nbsp 0183 32 API security is a set of practices and procedures that protect application programming interfaces APIs and the data they transmit from misuse malicious bot attacks
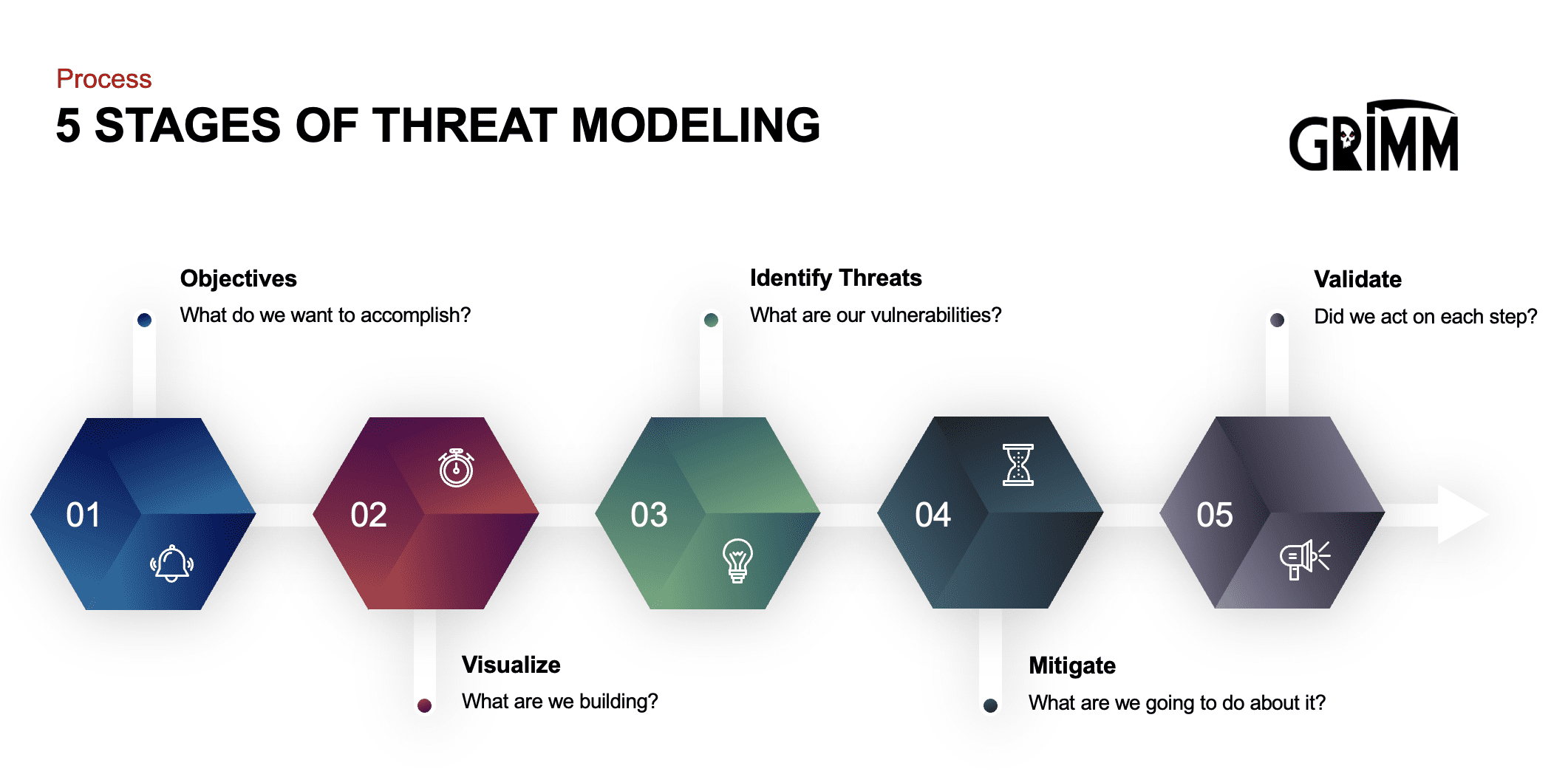
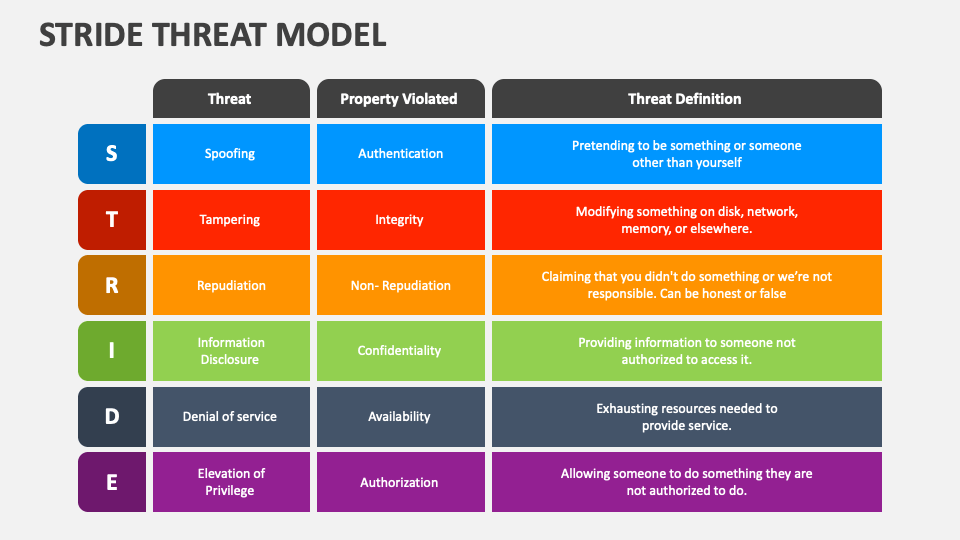
Stride Threat Model PowerPoint Presentation Slides PPT Template
SOAR for security orchestration automation and response is a software solution that enables security teams to integrate and coordinate separate security tools automate repetitive tasks What Is SOAR security Orchestration Automation And Response . Database security refers to the range of tools controls and measures designed to establish and preserve database confidentiality integrity and availability Oct 15 2021 nbsp 0183 32 Security controls are parameters implemented to protect various forms of data and infrastructure important to an organization Security controls refer to any type of safeguard or
Another Security Modeling And Threat Modeling Resources Cybersecurity Memo you can download
You can find and download another posts related to Security Modeling And Threat Modeling Resources Cybersecurity Memo by clicking link below
- Threat Modeling For Cloud Applications Secure Debug
- Top 5 Threat Modeling Methodologies Practical DevSecOps
- An Experience My Story
- Threat Modeling Basics
- Network Layer Model
Thankyou for visiting and read this post about Security Modeling And Threat Modeling Resources Cybersecurity Memo