Threat Modeling Cheat Sheet OWASP
Inspired by these commonalities and guided by the four key questions of threat modeling discussed above this cheatsheet will break the threat modeling down into four basic steps application decomposition threat identification and ranking mitigations and review and validation
Threat Modeling In Software Development DZone, Sep 12 2023 nbsp 0183 32 Threat modeling is a systematic approach to identifying and mitigating security threats early in the software development process It is essentially a risk management process that helps
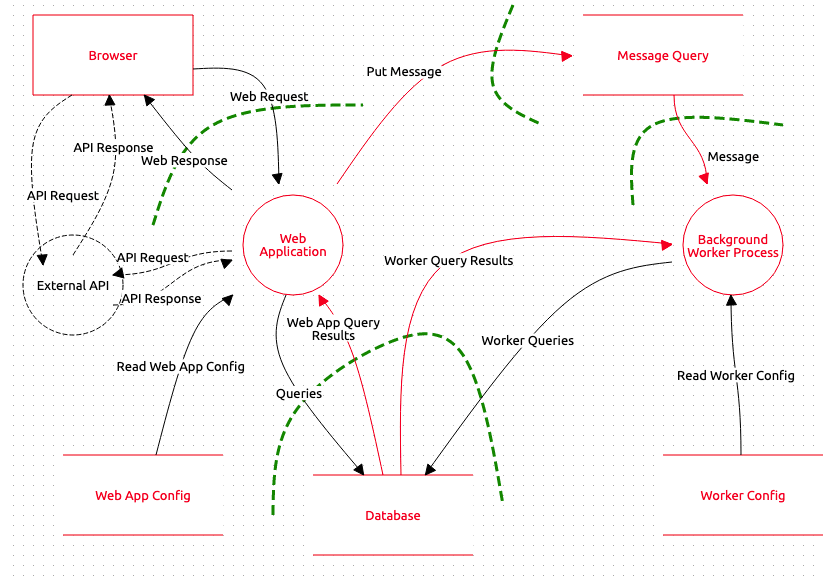
Threat Modelling Process In Cybersecurity Medium
Nov 21 2024 nbsp 0183 32 Threat modeling emerges as a critical strategy in identifying analyzing and mitigating potential risks before they can be exploited Threat modeling is a research driven approach that allows
Threat Modeling OWASP Foundation, Threat modeling works to identify communicate and understand threats and mitigations within the context of protecting something of value A threat model is a structured representation of all the information that affects the security of an application
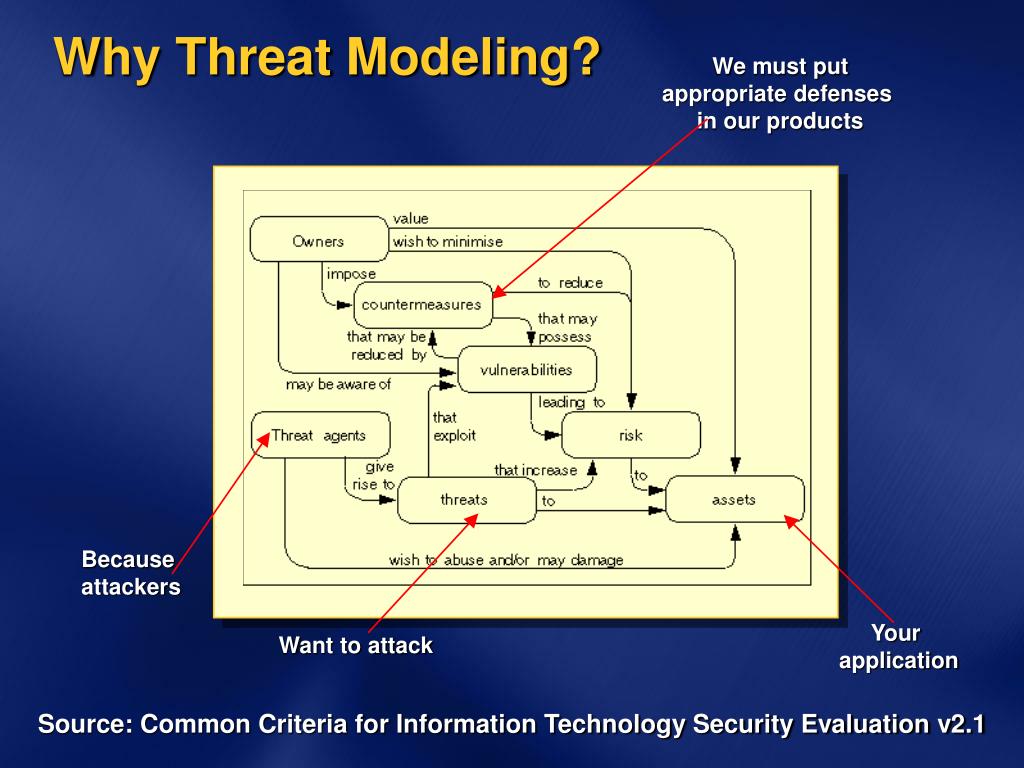
What Is Threat Modelling 10 Threat Identity Methods Explained
What Is Threat Modelling 10 Threat Identity Methods Explained, Mar 11 2025 nbsp 0183 32 Threat modeling is a process of predicting all potential threats to an organization s ecosystem and the vulnerabilities at risk of being explored by them Threat analysis however focuses on how an attacker could exploit vulnerabilities in order to

What Is Threat Intelligence Definition And FAQs HEAVY AI
A Strategic Guide To Threat Modelling For Today s Cyber Landscape
A Strategic Guide To Threat Modelling For Today s Cyber Landscape Nov 10 2023 nbsp 0183 32 Threat modelling helps you anticipate potential attacks and take proactive measures to protect yourself The main objectives of threat modelling are to identify potential threats assess
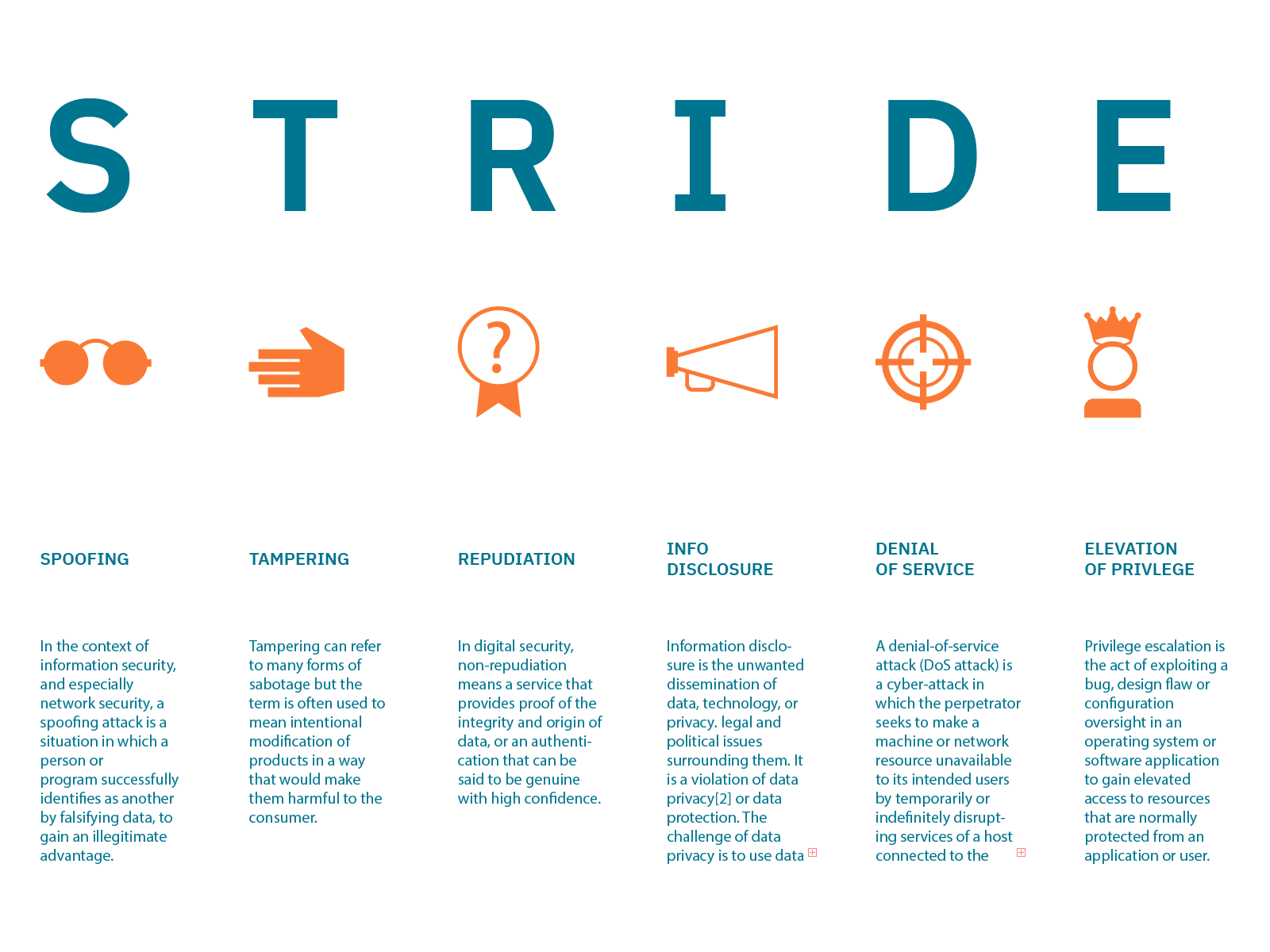
Software Threat Modeling Wwhrom
Threat modeling a proactive approach to identifying managing and mitigating potential security threats at design time plays a crucial role in the cybersecurity lifecycle of applications It involves predicting attacker behavior identifying potential security vulnerabilities in a system and defining effective countermeasures Ensuring Cyber Resilience The Critical Role Of Threat Modeling . In today s cybersecurity landscape security by design is becoming a standard in software development In this context threat modeling plays a critical role in identifying assessing and mitigating potential security vulnerabilities in software systems as they are built Threat modeling is the process of using hypothetical scenarios system diagrams and testing to help secure systems and data By identifying vulnerabilities helping with risk assessment and suggesting corrective action threat modeling helps improve cybersecurity and trust in key business systems
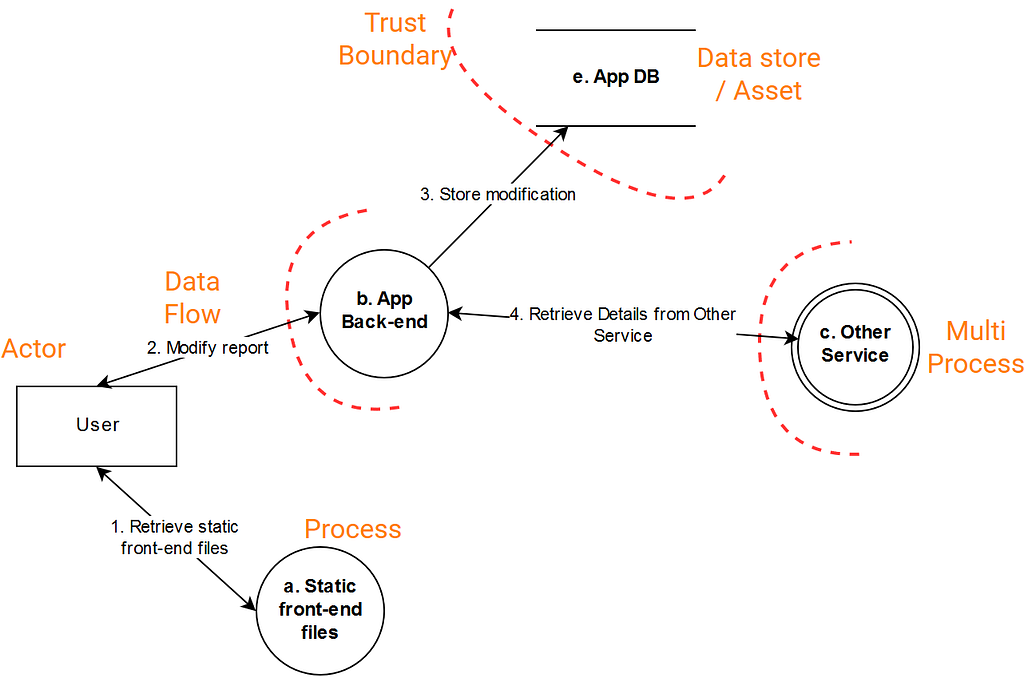
Another The Role Of Threat Modeling In Software Development A Cybersecurity you can download
You can find and download another posts related to The Role Of Threat Modeling In Software Development A Cybersecurity by clicking link below
- Cyber Threat Intelligence PowerPoint And Google Slides Template PPT
- Attacks And Threat Modeling By Wentz Wu ISSAP ISSEP ISSMP CISSP
- Threat Modeling Basics
- What Is Cyber Threat Modeling Importance Of Threat Modeling EC Council
- Threat Modeling Data Flow Diagrams
Thankyou for visiting and read this post about The Role Of Threat Modeling In Software Development A Cybersecurity