LINDDUN A Privacy Threat Analysis Framework KU Leuven
WEB order to help analysts determine the relevance of a threat for the system An example threat tree is presented in Fig ure 2 Each path of the threat tree indicates a valid attack path Note that some trees cascade For example the tree in Figure 2 shows the conditions that could lead to tampering threats against a process
Example Of A LINDDUN Threat Tree Linkability Of Data Flow , WEB Download scientific diagram Example of a LINDDUN threat tree Linkability of Data Flow from publication A Threat Model for Soft Privacy on Smart Cars Modern cars are

A LINDDUN Tutorial Lirias kuleuven be
WEB A more schematic overview of the different LINDDUN steps applied to an example is depicted in Figure 2 problem space and Figure 3 solution space Problem oriented steps First of all a data flow diagram is created based on system description which can be either high level at the requirements phase or a more detailed architecture step 1
Robles Gonz 225 lez Et Al A LINDDUN Based Framework For Privacy Threat , WEB that it provides an extensive catalogue of privacy specific threat tree patterns 14 and defines a mapping of most commonly known privacy enhancing technologies PET to identified privacy threats 1 LINDDUN is an acronym of these privacy threat categories Linkability Identifiability Non repudiation Detecta

A LINDDUN Based Framework For Privacy Threat Analysis On
A LINDDUN Based Framework For Privacy Threat Analysis On , WEB Jul 1 2020 nbsp 0183 32 The improvement of the LINDDUN framework proposed in K Wuyts 2015 leads to the improved methodology LIND D UN that is described in the tutorial Wuyts and Joosen 2015 and the corresponding updated LIND D UN privacy threat tree catalogue Wuyts et al 2014 We will use throughout the paper LINDDUN since we will consider
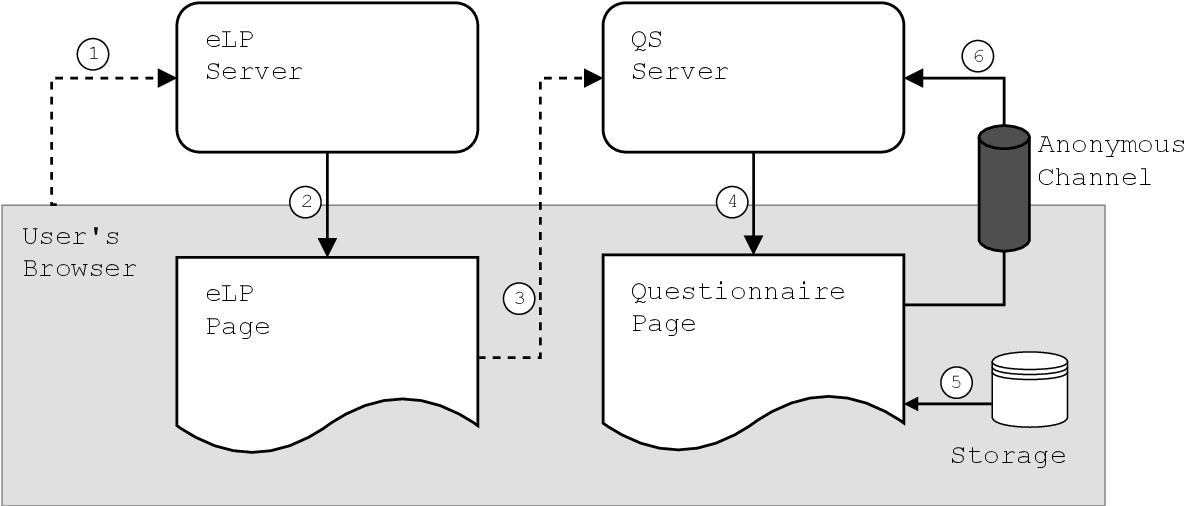
Figure 4 4 From A Browser based Anonymous Questionnaire System With
LINDDUN Privacy Engineering SecAppDev
LINDDUN Privacy Engineering SecAppDev WEB Step 2 Elicit threats Linkability An adversary is able to link two items of interest without knowing the identity of the data subject s involved Identifiability An adversary is able to identify a data subject from a set of data subjects through an

Figure 3 From Short Dynamic Group Signature Scheme Supporting
WEB threat categories encompassed in the LINDDUN acronym linkability identi ability non repudiation detectability disclosure of information unawareness non compliance LINDDUN consists of the following three steps 1 Model the system Typically a data ow diagram DFD 9 is used which is a very simple representa LINDDUN GO A Lightweight Approach To Privacy Threat Modeling. WEB STRIDE Security Threat Modeling Spoo ng of user idenSty Tampering RepudiaSon InformaSon disclosure Denial of service ElevaSon of WEB The examples are illustrations of linking identifying non repudiation detecting data disclosure unawareness and non compliance threats that can be expressed with one or more threat characteristics from the LINDDUN threat trees

Another Example Of A Linddun Threat Tree Linkability Of Data Flow From Wuyts you can download
You can find and download another posts related to Example Of A Linddun Threat Tree Linkability Of Data Flow From Wuyts by clicking link below
- Figure 2 2 From A Browser based Anonymous Questionnaire System With
- LINDDUN A Privacy Threat Analysis Frameworkkim wuyts LINDDUN LINDDUN
- Figure 1 From Are 140 Characters Enough A Large Scale Linkability
- Threat Modeling Process OWASP Foundation
- Example Of A LINDDUN Threat Tree Linking Download Scientific Diagram
Thankyou for visiting and read this post about Example Of A Linddun Threat Tree Linkability Of Data Flow From Wuyts