Threat Modeling OWASP Foundation
Threat modeling is a process for capturing organizing and analyzing all of this information Applied to software it enables informed decision making about application security risks In addition to producing a model typical threat modeling efforts also produce a prioritized list of security improvements to the concept requirements design
OWASP Developer Guide Threat Modeling In Practice OWASP Foundation, 4 1 1 Threat modeling in practice This section discusses Threat Modeling an activity described in the OWASP Software Assurance Maturity Model SAMM Threat modeling is part of the Threat Assessment security practice in the Design business function Much of the material in this section is drawn from the OWASP Threat Model project and the

Threat Modeling Cheat Sheet OWASP
Additionally the threat modeling process can be complex and time consuming It requires a systematic approach and in depth analysis which is often difficult to reconcile with tight schedules and the pressure to deliver new functionalities Development teams may feel a lack of tools and resources to support them in this task leading to
Threat Modelling Hacking The Design OWASP, What is Threat Modelling Threat modelling is a process by which potential threats can be identified enumerated and prioritised all from a hypothetical attacker s point of view The purpose of threat modelling is to provide defenders with a systematic analysis of the probable attacker s profile the most likely attack vectors and
Threat Modeling Explained A Process For Anticipating Cyber Attacks
Threat Modeling Explained A Process For Anticipating Cyber Attacks, Apr 15 2020 nbsp 0183 32 Threat modeling process and steps Each individual threat modeling methodology consists of a somewhat different series of steps and we ll discuss the nuances of each later in this article But
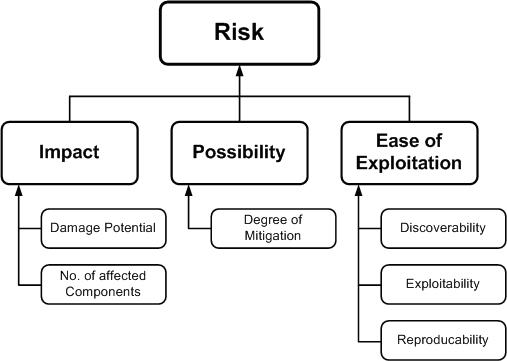
Threat Modeling Process OWASP Foundation
Threat Modeling OWASP
Threat Modeling OWASP Threat Anything that can cause harm Intent is irrelevant Risk Chance that a threat will cause harm Risk amount probability impact Risk will always be present in any system Countermeasure Control to reduce risk Reduction to an acceptable level Must be balanced against both risk and asset
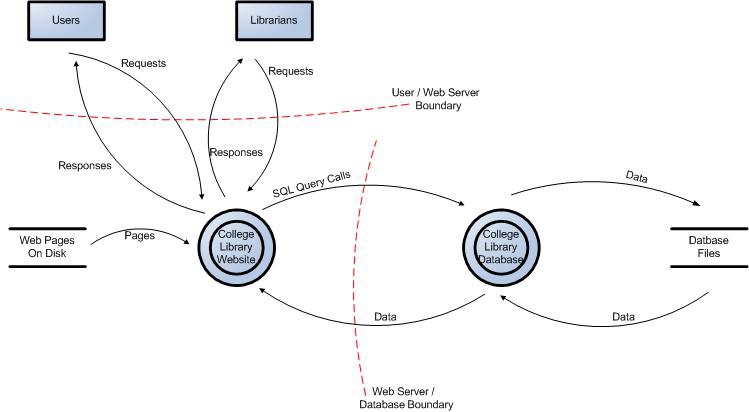
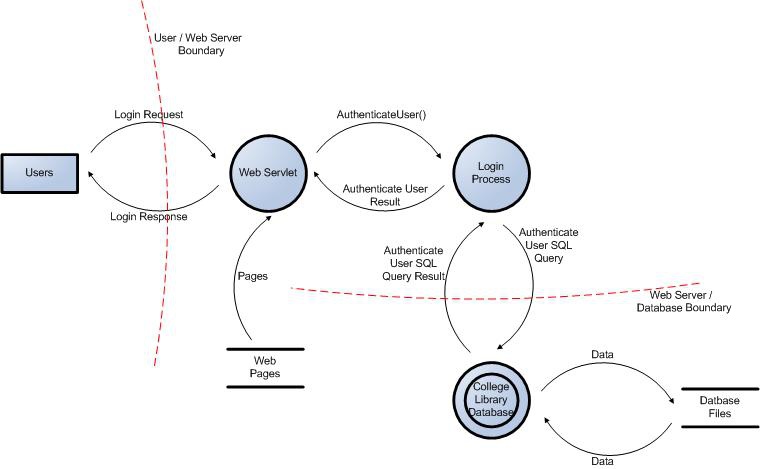
OWASP DevSecOps Guideline V 0 2 OWASP Foundation
The threat modeling process depends on a sequential series of actions Even though they can be performed individually they are interdependent so executing them together provides a more comprehensive view of the threat situation The steps tend to include Outlining the concern you have as it pertains to a specific system application or process What Is Threat Modeling How Does It Work Fortinet. The threat modeling process depends on the system under investigation Most business processes that rely on IT can benefit in some way Threat modeling allows security analysts to narrow the scope of threats to a specific system It removes the confusion about what threats are present and how to mitigate them It also gives the IT team the Threat modeling is a process for capturing organizing and analyzing all of this information Threat modeling enables informed decision making about application security risk In addition to producing a model typical threat modeling efforts also produce a prioritized list of security improvements to the concept requirements design or
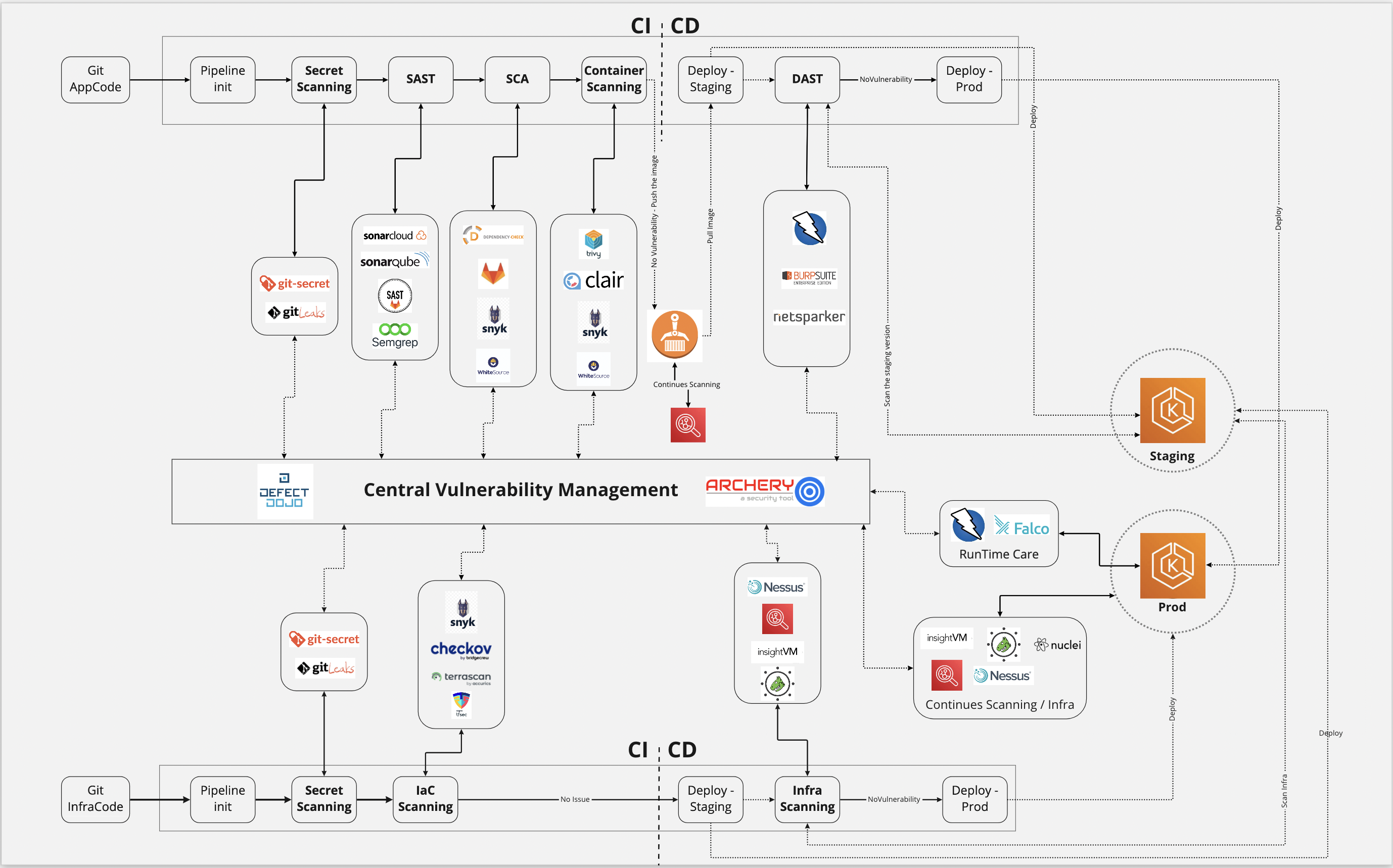
Another Threat Modeling Process Owasp Foundation you can download
You can find and download another posts related to Threat Modeling Process Owasp Foundation by clicking link below
- OWASP Security Culture OWASP Foundation
- Microsoft Free Threat Modeling Tool Imageslawpc
- The Role Of Threat Modeling In Software Development A Cybersecurity
- Threat Modeling OpenID Connect OAuth 2 0 For Beginners Using OWASP
- Threat Modeling The Why How When And Which Tools DevOps
Thankyou for visiting and read this post about Threat Modeling Process Owasp Foundation